Secure KVM switches are designed from the ground up as dedicated switching devices with every element conceived to prevent unauthorized access, ensure data isolation, and are optimized for accessing networks at different levels of security; especially useful for government, military, and defense operations. As departments and companies become more reliant on electronic systems, security concerns grow and new threats are identified, such as electronic emissions and power sources.
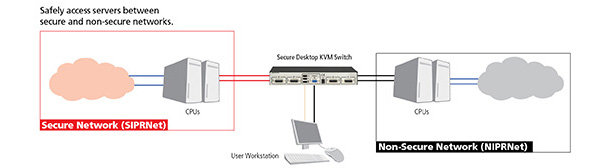
Photo courtesy of Blackbox
Having isolation between a Secure Network and a Non-Secure Network allows the user to access both systems from one user station thus saving space and costs.
Electronic emissions may pose a threat to secure environments as these stray signals provide a conduit by which sensitive information could easily leak into the wrong hands. Video cables, for example, can emit strong emissions that can be collected and duplicated to view the same image elsewhere. Another threat includes power sources that can be used to conduct data back into a mains electricity supply and this in turn can be picked out using sensitive devices outside of the system’s physical location. Typical KVM switches that do not actively combat these leakage threats may therefore pose a significant security risk.
Secure KVM Requirements & Features
CC Protection Profiles for KVM Switches
Using the Protection Profile for Peripheral Sharing Switches, CC (Common Criteria) evaluates KVM (Keyboard-Video-Mouse) switches, KM (Keyboard-Mouse) switches, KVM splitters (Reverse KVMs), and Multi-viewers. NOTE The Peripheral Sharing Protection Profile is not suitable for the evaluation against over-IP, network-attached switches, and matrix switches.
There are two main versions of the PPS that are commonly used in modern Secure KVM switches:
- Protection Profile for Peripheral Sharing Switch Version 3.0
- Protection Profile for Peripheral Sharing Switch Version 2.1
If you’re interested in learning more about particular KVM product specifications, check out our partner’s resources at KVM Switches Online.
CC Evaluation & Certification
“By awarding a Common Criteria certificate, the CC Certification Body (CCS) asserts that the product complies with the security requirements specified in the associated security target. A security target is a requirements specification document that defines the scope of the evaluation activities. The consumer of certified IT products should review the security target, in addition to this certification report, in order to gain an understanding of any assumptions made during the evaluation, the IT product’s intended environment, its security requirements, and the level of confidence (i.e., the evaluation assurance level) that the product satisfies the security requirements.” Common Criteria (2)

Photo courtesy of https://www.commoncriteriaportal.org/ccra/members/
The international Common Criteria Recognition Arrangement (CCRA) brings together 26 nations that have agreed to accept a unified approach to the evaluations of IT product information assurance and security. Evaluations in the United States are performed by the commercial Common Criteria (CC) testing laboratory under the oversight of the National Information Assurance Partnership (NIAP) — a collaboration between Nation Institute of Standards and Technology (NIST) and the National Security Agency (NSA).
Read a few considerations for choosing your best fit KVM Switch
What are EAL 2 & EAL 4?
The EAL (Evaluation Assurance Level) is assigned a number based on the set of security testing criteria as classified by Common Criteria (CC). Each level has a unique rubric for testing security profiles involving function, structure, method, design, documentation, and/or use analysis. NOTE A higher EAL rating does not indicate a higher level of security; it simply indicates a more rigorous evaluation process.
The two main CC Assurance Level evaluations typically used for Secure KVM Switches are EAL 2 and EAL 4. A summary of these evaluations involve:
EAL 2: Structurally Tested. Anaysis of the security functions using a functional and interface specification and the high level design of the subsystems of the TOE. Independent testing of the security functions, evidence of developer “black box” testing, and evidence of a development search for obvious vulnerabilities.
EAL 4: Methodically Designed, Tested and Reviewed. Analysis is supported by the low-level design of the modules of the TOE, and a subset of the implementation. Testing is supported by an independent search for obvious vulnerabilities. Development controls are supported by a life-cycle model, identification of tools, and automated configuration management. National Technical Authority for Information Assurance (5)
What is the TEMPEST Certification?
TEMPEST is a specification created by NSA and NATO for certifying IT systems against the possibility of spying through leaking emanations such as electrical signals, radio waves, sounds, and vibration. While most of TEMPEST covers electrical signal and radio wave emanation, it also stringently covers sound and mechanical vibration. “For example, it is possible to log a user’s keystrokes using the motion sensor inside smartphones.” (4)
Many specifics of the TEMPEST standards are classified and therefore unavailable for public review. What we do know is TEMPEST protects equipment from eavesdropping by shielding, filtering, masking, and/or limiting the distance of transmissions. Note: TEMPEST covers the entire IT system, not individual components of the system.
There are three standard levels of TEMPEST protection:
- Level 1 is the most strict standard where it is assumed that the attacker could gain physical access to the device.
- Level 2 and 3 are more relaxed assuming the attacker could get within 20 meters (65 feet) or 100 meters (330 feet) respectively.
Questions & Concerns about Secure KVMs?
Start a conversation. We want to listen.
References:
(1) National Information Assurance Partnership (NIAP)
(2) The Common Criteria (CC)
(3) Adder – “Tempest and EAL4+ qualified secure KVM switches launched”
(4) Wikipedia – “Tempest (codename)”
(5) National Technical Authority for Information Assurance – CC Assurance Levels
Other Resources:
KVM Switches Online – NIAP-Certified Secure KVM Switches
NIAP-CCEVS – Documents and Guidance




